Activating the NoSpamProxy Sandbox Service
Option 1: Adapt an existing action
- Go to Configuration > Content filter > Content filter actions.
- Open an existing action for inbound emails.
- Switch to the Attachments tab.
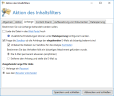
- Check the box next to Query the sandbox if attachments of inbound emails are known to be malicious.
If this option is activated, NoSpamProxy compares the hash values of attachments with hash values already in the sandbox database. The retrieval of the hash values is unrestricted and without deduction of purchased licences.
- Optionally, tick the check box next to Upload unknown files to sandbox for analysis.
- Select either Reject the email permanently (recommended) or Remove the attachment and deliver the email.
If this option is activated, files unknown to the sandbox are uploaded to the sandbox for analysis. The upload of files is limited to 20 files per user and month. See Further information.
NOTE: The Sandbox Service is only available if you have selected Allow attachment on the Action tab.
Option 2: Create a new content filter action
Creating a new content filter action is particularly useful if you want to restrict the sandbox check to individual file types.
- Go to Configuration > Content filter > Content filter actions.
- Click Add.
- In the General dialog box, enter a name for the new action and select SMTP emails.
- In the Action dialog box, select Allow attachment.
- Make the settings for the sandbox as described above for the Attachment tab.
- Make all other settings for the new action as desired.
- Click Finish.
You now have to trigger the adjusted or newly created action via a content filter entry.
Supported file types
General
- Executable files
- Executable files for Windows
- Microsoft Office
- Microsoft Excel (all)
- Microsoft PowerPoint (all)
- Microsoft Word (all)
- Text
- HTML
- PDF document
- PDF document with URLs
- Rich text format
- Rich text format with OLE objects
- Scripts
- .js
- .vbs
- .ps1
-
Archives and compressed files
-
7Zip-compressed file
-
ACE-compressed files
- AR-compressed files
-
ARJ-compressed file
-
BZIP2-compressed files
-
GZIP-compressed file
-
RAR-compressed files
-
TAR-compressed files
-
Windows Installer file
-
ZIP-compressed file
-
*.alz
-
*.cab
-
*.z
-
*.zoo
-
We strongly recommend using an allowlisting approach to content filtering. This recommendation applies in particular to the use of the NoSpamProxy sandbox service.
An example: Even if an "Executable file for Windows" is supported by the sandbox, the question arises whether one wants to allow this potentially dangerous file type for one's own company at all. In this case, it makes more sense to generally reject this file type and thus also save the upload to the sandbox.
If a file should be classified as unsuspicious by the sandbox service, the respective e-mail is delivered.
Delivery delay
When a file is uploaded to the sandbox, the email is not accepted in the first step but temporarily rejected so that the sending email server delivers it again. Temporary rejection is applied here because the analysis on the sandbox array takes a certain amount of time, but this should be completed after about five minutes when a new delivery attempt is made.
This means a delivery delay for the delivery, which must be observed accordingly. Thus, we recommend that you carefully check which files should really be sent to the sandbox. Note the following option if time-critical processes or mailboxes exist in the company:
- Is a sandbox hash query sufficient instead of a full analysis (sandbox upload)?
- It is possible to create different actions in the content filter to configure different actions for "Trusted emails" and "Untrusted emails". Here you can distinguish between a sandbox upload and a sandbox hash query.
- Office documents can be converted into a secure PDF document by Content Disarm and Reconstruction (CDR) if necessary. See Notes on Content Disarm and Reconstruction (CDR).
See
Further information
TIP: Read our blog article The Time for Proper Email Firewalls Has Come.
NOTE: The number of complete analyses (sandbox upload) by the sandbox service is limited to 20 per user and month. The billing is not user-based. For example, with 100 users, a total of 2000 complete analyses can be performed, regardless of how many analyses are performed by each user. We recommend that you configure the filters in NoSpamProxy® in such a way that an analysis by the Sandbox Service is only performed if emails have not already been rejected by upstream filter levels. If the limit is exceeded, additional costs may be incurred.
TIP: To limit the check by the sandbox service to individual file types, an additional content filter action should be created that is only applied to certain file types.