Level of trust configuration
To configure Level of Trust, proceed as follows:
- Go to Configuration > Advanced settings > Level of Trust configuration.
- Click Modify.
- Make the settings on the individual tabs (see below).
- Click Save and close.
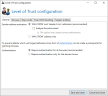
- Sender address evaluation Determines which addresses are used for the analysis if the MAIL FROM address and the header FROM address are different. If both addresses are verified, the email will be rejected if either address is not trustworthy.
- 'MAIL FROM' and 'Header From' addresses (recommended)
- (Optional) The entire email (may affect server performance)
NOTE: If the entire email is analysed, it is evaluated using all the filters configured in the respective rule. The result of this evaluation is correspondingly more accurate than the sole evaluation of 'MAIL FROM' and 'Header-From' and can overrule the latter evaluation. As all emails are received in full, this option can have a negative impact on server performance.
- (Optional) The entire email (may affect server performance)
- 'MAIL FROM' addresses only
- 'MAIL FROM' and 'Header From' addresses (recommended)
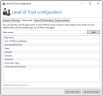
- Authentication Determines whether successful authentication through DKIM, S/MIME and SPF checks is a prerequisite for all bonuses or only for the domain bonus (see Bonuses tab).
- Address pairing Determines by how many points the trust between a sender and a recipient is increased per email. With the slider you can set a value between 0 and 200. One point corresponds to (-0.1) points for the Spam Confidence Level (SCL). For each email to external addresses, not only the so-called address relationship bonus is increased, but also a bonus for the respective recipient domain.
- Domain pairing Determines how many points the domain bonus is increased by. This value should be smaller than the bonus for address relationships. You can set a value between 0 and 200 with the slider. One point corresponds to (-0.1) points for the Spam Confidence Level (SCL).
Smart DSN handling checks Delivery Status Notifications (DSNs) to local addresses. Since NoSpamProxy knows which emails have been sent from the company, it can also determine whether a corresponding email has left the company for the DSN that is currently available.
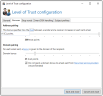
- Smart DSN handling Determines if and how intelligent DSN filtering applied.
- Automatic NoSpamProxy first checks whether there are any elements in the Level of Trust database that are older than seven days. Only then does NoSpamProxy evaluate inbound DSNs.
- Enabled NoSpamProxy evaluates the DSN in every case; even if no data records exist in the Level of Trust database.
- Disabled The intelligent DSN filtering is disabled.
A DSN arrives and NoSpamProxy determines that the original message for that DSN was sent from schmidt@example.com to schulze@netatwork.de. NoSpamProxy now checks whether there is an address pair schmidt@example.com/schulze@netatwork.de in the Level of Trust database.
If this is not the case, the DSN in question may not be valid and receives penalty points. If a suitable address pair is found, the DSN receives bonus points. For this analysis to take place, two conditions must be met:
- There must be an RFC-compliant DSN. This means that the original message is attached to the DSN so that NoSpamProxy can determine the original address pair.
- It must be ensured that the mail gateway knows all emails to external addresses. In networks with distributed Internet connections, this can be a problem under certain circumstances.