Automatic user import via Azure Active Directory
- Go to Identities > Automatic user import.
- Click Add.
- Enter a name for the user import and configure the status of the user import.
- Enter the name of your Azure tenant.
NOTE: You must grant tenant-wide administrator permission to set up automatic user import. Follow the instructions in the dialog.
- (Optional) Click Add to add a group stored in your Azure Active Directory and configure it to assign different functions to the respective users:
- General Select the group you want to add.

- Content filtering Applied to attachments contained in inbound and outbound emails. See Changing content filter settings.
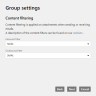
- CxO Fraud Detection Uses the names of all group members to detect phishing attacks. See Automatic user import via Azure Active Directory
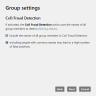
- Language Select a language for email hints and email notifications that are added to emails.
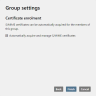
- Certificate Request Automatically requests S/MIME certificates for members of this group.
- General Select the group you want to add.
- Click Finish.
TIP: Click Execute now to trigger the user import manually.
NOTE: NoSpamProxy does not support public folders, as these are also no longer supported by Azure Active Directory.
Notes
- In order to request managed certificates for all users, you must have licensed a sufficient number of users. For example, if the added group contains more users than there are licences available, managed certificates will not be requested. In this case, the administrator receives a notification email.
- In order for managed certificates to be requested for users, the user attribute email address must be stored for these users.
CxO fraud detection is designed to detect and defend against phishing attacks that misuse the identity of particularly exposed decision-makers in companies. It compares the sender name from 'Header-From' and 'MAIL FROM' in inbound emails with the names of corporate users.
Fake emails sent to you on behalf of superiors or employees are intercepted in this way.
During the inspection different variants of the sender name are included in the comparison. Here are some examples:
- Jane Doe
- Doe Jane
- JaneDoe
- DoeJane
All corporate users that you want to use for CxO Fraud Detection must be activated individually via Active Directory groups.