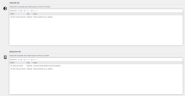
Rules
Here you will find an overview of the available rules. These managed rules cover specific use cases, which are documented by name and description. These rules become active if the respective email is within the configured scope. If none of the managed rules are applied, the email is processed based on the standard set of rules.
Configuring the scope of a rule
- Go to Configuration > Rules.
- Double-click the rule you want to edit or select it and click Edit.
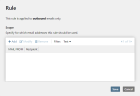
- Click Add.
- Restrict the scope of the rule for sender (MAIL FROM) and recipient as desired.
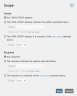
- Click Save.
EXAMPLE: If you enter *user@example.com, this pattern corresponds to all email addresses ending in user@example.com. If you enter *@example.com all addresses from the domain example.com match. If you enter *.example.com, all subdomains of example.com will match.
NOTE: In order to use groups, you must first add them to a user import. See Automatic user import via Azure Active Directory.
Properties of the rules
NOTE: The malware scanner will be applied to all inbound and outbound emails.
NOTE: Unlike our standard rules, the predefined rules in which you can set entries are filtered to the Corporate domain. This means that we also accept emails for users who may not be known as corporate users.
Inbound
Internal communication
This inbound default rule enables communication between two internal systems when using company domains. Provided that the appropriate licence has been obtained, important actions such as decryption and signature verification are carried out without taking into account certificate chains, the application of inbound disclaimers and malware checks.
Malware scanning and content filtering
This rule includes malware scanning and content filtering of attachments, but does not check the content of the email or the reputation of the sender. Provided that the appropriate licence has been obtained, emails are decrypted without taking the certificate chain into account and the inbound disclaimer is applied.
Malware scanning, no content filtering
This rule only includes the malware scan of attachments, but does not check the content of the email or the reputation of the sender. Provided that the appropriate licence has been obtained, emails are decrypted without taking the certificate chain into account and the inbound disclaimer is applied.
WARNING: This rule should only be used if absolutely necessary.
All other inbound emails
This inbound default rule is always active and includes all licenced checks that offer the highest level of email protection.
Soft check
This rule carries out a significantly reduced spam and reputation check of the sender. Provided that the appropriate licence has been obtained, important actions such as decryption and signature verification are carried out without taking into account certificate chains and the application of incoming disclaimers. A malware check, attachment check and blocklist check are also carried out. Level of Trust, URL Safeguard, the Core Anti Spam Engine and CxO Fraud are no longer taken into account.
Medium check
This rule performs a slightly reduced spam and reputation check of the sender and is limited to the main domain. Provided that the appropriate licence has been obtained, important actions such as decryption and signature verification are carried out without taking certificate chains, the application of inbound disclaimers and spam and malware checks into account. The URL Safeguard is no longer active.
Block list
This rule immediately rejects inbound emails without taking any exceptions into account.
Decryption allowlist
This rule corresponds to the default rule All other inbound emails, but allows encrypted emails that NoSpamProxy cannot decrypt to pass through.
NOTE: Public keys are not collected from digital signatures.
Outbound
NOTE: For outbound connections, NoSpamProxy Cloud always attempts to establish a TLS connection.
All outbound emails
This outbound default rule is always active and includes all licensed checks and actions that provide the highest email reputation. Emails encrypted by the client are rejected; emails that have already been digitally signed cannot be additionally signed with DKIM. Furthermore, where possible, a digital signature and/or encryption is applied and the content is checked.
Plain text
This rule sends all emails as text emails without signing and encryption. TLS will continue to be used if available.
Forced encryption
This rule enforces encryption. If no key material can be found, NoSpamProxy Cloud applies PDF Mail (i.e. PDF encryption). If the PDF password does not exist, the recipient is prompted to set a password.
Encryption allowlist/Ausnahme für Verschlüsselung
This rule corresponds to the All outbound emails rule, but allows emails already encrypted by the client to pass through.
Signing only/Ausschließlich signieren
This rule signs emails, but never encrypts them with S/MIME, PGP or PDF Mail. TLS will continue to be used if available.
No 32Guards/Kein 32Guards
This rule does not perform a check with 32Guards. It is only suitable for cases where there is a false positive from 32Guards. See Reporting false negatives and false positives.
NOTE: Under no circumstances should you use this rule permanently.
No 32Guards, plain text email
This rule sends all emails as text emails without signing and encryption and without a 32Guards check. TLS will continue to be used if available. It is only suitable for cases where there is a false positive from 32Guards. See Reporting false negatives and false positives.
NOTE: Under no circumstances should you use this rule permanently.