Step 4: Configuring the key management service
To set up the sending and receiving of AS4 messages in NoSpamProxy, you must first enter the service address of the key management service and optionally add a hardware security module (HSM) in NoSpamProxy.
NOTE: The key management service is used for the secure storage of private keys. For maximum security, we still recommend the use of an HSM. See below, Who needs to use an HSM?
Configuring the service address
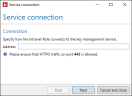
- The service address is the address at which the Intranet Role connects to the key management service.
- In the NoSpamProxy Command Centre, go to NoSpamProxy components > Key management service and click Modify.
- Enter the service address under Connection.
NOTE: The default address is https://localhost:6064. In any case, make sure that HTTPS traffic is permitted on port 6064.
- Under Credentials, enter the administrative user information for the service.
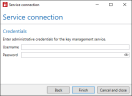
- Click Finish.
(Optional) Adding an HSM
If you also want to use an HSM to store your private keys, add it here.
- In the NoSpamProxy Command Centre, go to Configuration > NoSpamProxy components > Key management service.
- Under Key storage, click Modify.
- Tick the Additionally use a Hardware Security Module (HSM) [...] box.
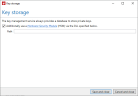
- Enter the path to the HSM DLL file.
- Click Save and close.
The Configured tokens area now appears under Key management service.
The following requirements must be met before you can use an HSM to store your private keys:
- The HSM must support the PKCS #11 standard.
- The HSM must use the Elliptic Curve Brainpool P256r1 standard for key generation (CKM_EC_KEY_PAIR_GEN).
- The HSM must use the key derivation function SP-800 (CKD_SHA256_KDF_SP800) for key derivation (CKM_ECDH1_DERIVE).
(Optional) Configuring a token
If you are using an HSM and have added it, you can access the tokens of the HSM and configure the desired token.
- Under Configured tokens, click Modify.
- Under Token, select the desired token from the drop-down menu.
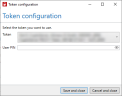
- Enter the corresponding PIN under User PIN.
- Click Save and close.
The HSM is now connected.
Frequently asked questions
With regard to the use of an HSM, the version of the Smart Metering PKI certificate policy dated 25 January 2023 (version 1.1.2) states that "[...] passive EMT cryptographic modules [must] be used that are at least compliant with the Key Lifecycle Security Requirements - Security Level 1. [...] Each market participant must derive the specific requirements for the cryptographic modules for itself in accordance with the security concept to be drawn up by it."
Passive external market participants (EMT) are defined in the Smart Metering PKI certificate policy 1.3.3.4 as market participants that receive or exchange data from the smart metering gateways (SMGWs) but do not control these devices.
An EMT that uses an SMGW to address downstream devices (Controllable Local Systems, CLS) is referred to as an active EMT.
Cryptographic modules of security level 1 can be operated as software or servers with two-factor authentication and physically restricted access. A random number generator of classes NTG.1, DRG.4 or PTG.3 in accordance with AIS 20/31 must be used to generate random numbers for key generation as well as for signature and encryption.